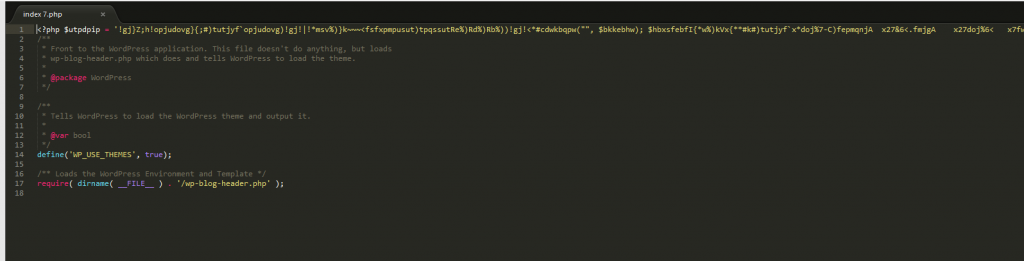
Note: This only works if the scripts are injected to the first line of every PHP files.
First backup the files
$ tar -zcvf public_html.infected.tar.gz public_html
Then go inside public_html to execute the code there
$ cd public_html
Find all files with .php extention and execute the sed command.
sed will do an infile search and replace. -i will backup the file to be edited and add .infected suffix.
'1 s/.*/<?php/' does search in first line from .* (means all of first line) and replace with <?php
Note: There’s a possibility that the site may function, so be ready to fix it.
The problem I encountered with this is that few php files that only have html contents are having errors bec of <?php in the first line.
Check the server log for details errors.
Another error I encountered from wordpress pages is that <?php get_header();?> in the first line is replaced with <?php
Execute the cleanup code below
$ find . -type f -name "*.php" -exec sed -i.infected '1 s/.*/<?php/' {} \;
Check the command has no adverse effect on the site.
After checking the site is still working, delete infected files
$ find . -type f -name "*.infected" -delete
